Safe Schools, Smart Data: AI Detection and Cybersecurity
DESCRIPTION
Revolutionize your approach to student and staff safety within your school/institution.
Tailored for educators, school administrators, and mobility coordinators who must navigate the complex digital environment of modern schooling. We move beyond basic cyber-awareness to focus on the infrastructure of risk and defense, ensuring compliance and proactive protection.
You will gain a foundational understanding of the Data Lifecycle, how seemingly innocent school data is collected, stored, and ultimately used to train and weaponize AI models, creating risks like deepfakes and predictive profiling.
The course provides hands-on, actionable strategies for securing institutional networks, managing cross-border data protection (with an additional focus on spreading your Erasmus+ mobility online), and teaching responsible Digital Citizenship to all members of the school community.
This program blends theoretical insights into data ethics and legal compliance (like GDPR) with practical training on threat detection, incident response planning, and creating "Privacy-by-Design" school protocols.
By the end of this course, you will be equipped to transform your school into a proactively safe digital environment, protecting your community from sophisticated AI-driven threats.
Learning Objectives:
Understand the full journey of student and staff data from collection to deletion, identifying vulnerabilities at each of the five stages (Collection, Storage, Processing, Sharing, Deletion).
Implement mandatory strategies to reduce unnecessary data collection, storage, and sharing across administrative, teaching, and marketing tasks.
Manage Cross-Border Data: Execute best practices for data protection during international mobility (e.g., Erasmus+), ensuring compliance with varying global standards and legal frameworks.
Recognize and respond to emerging threats like synthetic media (deepfakes, voice cloning) and advanced social engineering (phishing, vishing).
Implement Network Safeguards: Establish and audit core cybersecurity safeguards, including robust password policies, secure Wi-Fi protocols, and effective Access Control Lists (ACLs).
Create simplified, school-specific protocols for responding immediately to data breaches, ransomware attacks, or unauthorized data sharing incidents.
Use practical, hands-on techniques (image blurring, metadata removal, strategic framing) to document school life and promote successes without compromising student identities.
Critically evaluate third-party educational technologies (EdTech) for privacy compliance, data security, and potential AI-training risks before adoption.
Lead staff and student training sessions on responsible digital behaviour, including the rationale behind The 2-Week Rule for travel posting and the dangers of "Sharenting," and teach the Decision Firewall rule-set.
Methodology
Interactive Lectures: Introduce key concepts (Data Lifecycle, AI risks) using accessible language and the "iceberg" and "ship steering" metaphors.
Hands-On Practice & Drills: Engage in guided, scenario-based activities, including Phishing Drills, MFA Setup, Data Minimization Audits, and Policy Drafting.
Case Study Analysis: Analyze real-world examples of school data breaches and AI misuse to understand the tangible impact of poor security practices.
Collaborative Policy Development: Work in teams to apply course concepts directly to the creation and refinement of existing school digital and mobility policies.
Resource Toolkit Creation: Participants will leave with a personalized toolkit of checklists, vetting forms (for EdTech), and incident response templates ready for immediate use.
-
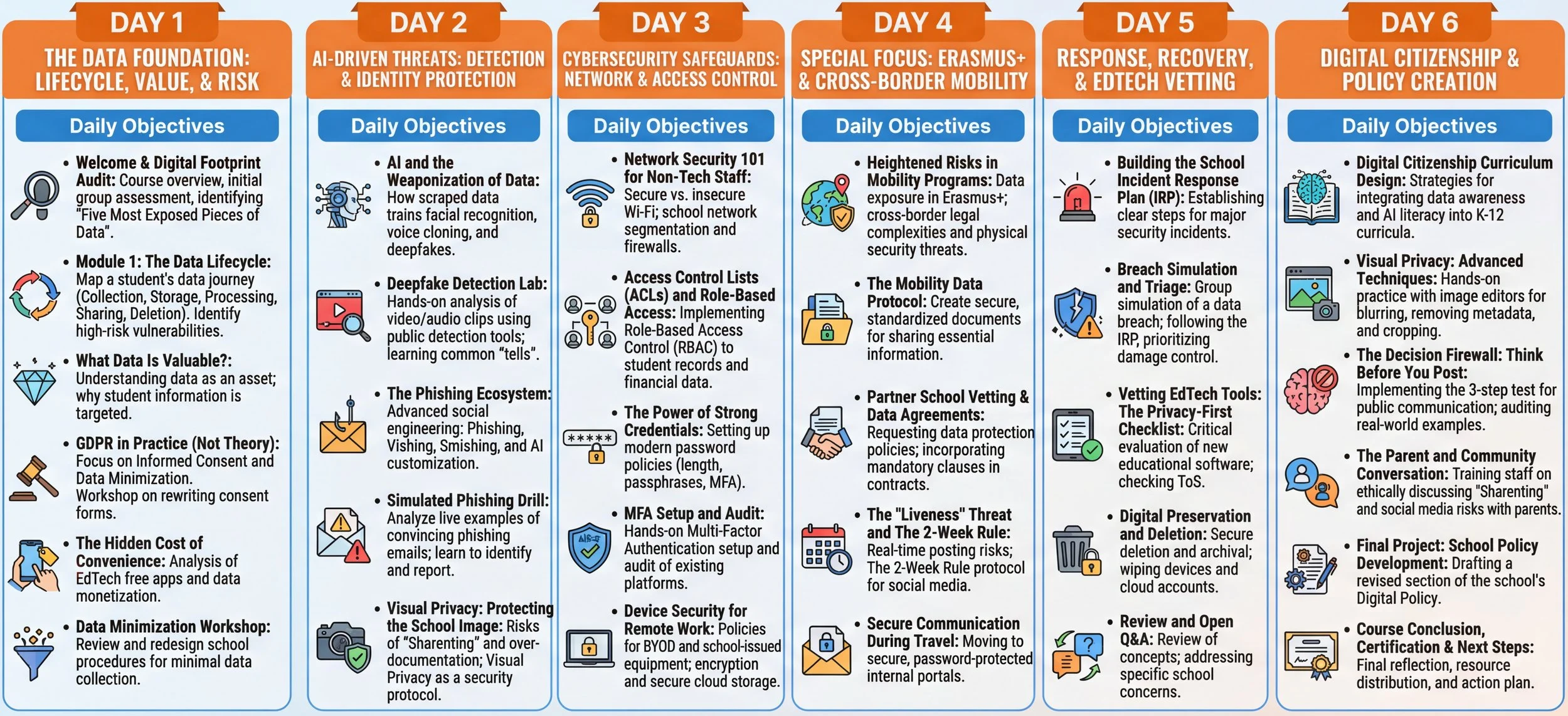
9:00–9:30 Welcome & Digital Footprint Audit
Course objectives, and initial group assessment of current school digital policies. Identify the school's "Five Most Exposed Pieces of Data."
9:30–10:30 Module 1: The Data Lifecycle
Hands-On Activity: Map a student's data journey from enrollment to graduation. Analyze the five stages (Collection, Storage, Processing, Sharing, Deletion) and identify 3 high-risk vulnerabilities in their current system.
10:30–11:00 What Data Is Valuable?
Understanding data as an asset: why student names, photos, and grades are attractive targets for commercial AI trainers and criminals.
11:15–12:00 GDPR in Practice (Not Theory)
Focus on Informed Consent and Data Minimization. Workshop on rewriting overly broad consent forms to comply with ethical and legal standards.
12:00–13:00 The Hidden Cost of Convenience
Discussion and analysis of popular free apps (EdTech) and how they monetize student/staff data (the trade-off).
13:00–14:00 Data Minimization Workshop
Hands-On Activity: Review school procedures and redesign them to collect the absolute minimum required data.
-
9:00–10:00 AI and the Weaponization of Data
How scraped school data trains facial recognition, voice cloning, and deepfake models. The threat of digital identity theft for staff and students.
10:00–11:00 Deepfake Detection Lab
Hands-On Activity: Use public deepfake detection tools to analyze video/audio clips. Learn common "tells" (unnatural blinking, inconsistent shadows, poor lip-sync) in synthetic media.
11:15–12:00 The Phishing Ecosystem
Advanced social engineering: Phishing, Vishing (voice calls), and Smishing (SMS). How AI customizes attacks based on public profiles.
12:00–13:00 Simulated Phishing Drill
Hands-On Activity: Analyze live examples of convincing, targeted phishing emails. Learn to identify and report suspicious communication immediately.
13:00–14:00 Visual Privacy: Protecting the School Image
The risks of "Sharenting" and over-documentation. Introduction to the concept of Visual Privacy as a security protocol.
-
9:00–10:00 Network Security 101 for Non-Tech Staff
Understanding the difference between secure (WPA3) and insecure (open) Wi-Fi. Basics of school network segmentation and firewalls.
10:00–11:00 Access Control Lists (ACLs) and Role-Based Access
Why not all staff need access to all data. Strategies for implementing Role-Based Access Control (RBAC) to student records and financial data.
11:15–12:00 The Power of Strong Credentials
Setting up and enforcing a modern password policy (length over complexity, passphrases, MFA).
12:00–13:00 MFA Setup and Audit
Hands-On Activity: Set up Multi-Factor Authentication (MFA) on a demonstration account. Review and audit their own existing MFA setup across professional platforms.
13:00–14:00 Device Security for Remote Work
Policies for staff personal devices (BYOD) and school-issued equipment. Encrypting laptops and secure cloud storage practices.
-
9:00–10:00 Heightened Risks in Mobility Programs
Why Erasmus+ participants face increased data exposure: cross-border legal complexities and physical security threats from location sharing.
10:00–11:00 The Mobility Data Protocol
Hands-On Activity: Create a secure, standardized document for sharing travel rosters, accommodation, and medical contacts only with essential personnel.
11:15–12:00 Partner School Vetting & Data Agreements
What to request from partner institutions regarding their data protection policies before a project starts. Incorporating a mandatory data protection clause in partnership contracts.
12:00–13:00 The "Liveness" Threat and The 2-Week Rule
Understanding how real-time posting reveals patterns and creates physical security risks for travelers and empty homes. The 2-Week Rule protocol for social media.
13:00–14:00 Secure Communication During Travel
Moving from unsecured communication tools (WhatsApp, public groups) to secure, password-protected internal portals (e.g., private school-vetted platforms).
-
9:00–10:00 Building the School Incident Response Plan (IRP)
Establishing clear, concise steps for What to Do First during a major security incident (e.g., breach, ransomware, lost device).
10:00–11:00 Breach Simulation and Triage
Hands-On Activity: Group simulation of a data breach scenario (e.g., staff credentials leaked). Participants must follow the IRP, prioritize damage control, and draft required notification to stakeholders.
11:15–12:00 Vetting EdTech Tools: The Privacy-First Checklist
A critical evaluation process for new educational software. Checking Terms of Service (ToS) for data collection, storage location, and third-party sharing.
12:00–13:00 Digital Preservation and Deletion
The final stage of the Data Lifecycle: secure deletion and archival. When and how to securely wipe devices and cloud accounts.
13:00–14:00 Review and Open Q&A
Review of all security and data minimization concepts learned so far. Addressing specific school concerns.
-
9:00–10:00 Digital Citizenship Curriculum Design
Strategies for integrating data awareness and AI literacy into existing K-12 curricula (not just an IT lesson).
10:00–11:00 Visual Privacy: Advanced Techniques
Hands-On Activity: Practice with image editors to quickly blur faces, remove metadata from photos, and crop images for safe, non-identifiable school marketing.
11:15–12:00 The Decision Firewall: Think Before You Post
Hands-On Activity: Implementing the 3-step test for all social media posting and public communication. Participants audit 5 real-world school posts using the firewall: The Grandma Test, The Future Employer Test, and The Screenshot Test.
12:00–13:00 The Parent and Community Conversation
Training staff on how to ethically discuss "Sharenting" and the risks of public social media with parents. Using accessible metaphors (like the "iceberg" analogy).
13:00–13:30 Final Project: School Policy Development
Hands-On Activity: Teams draft a revised section of their school's Digital Policy incorporating at least one new AI-driven threat and one Erasmus+ safeguard.
13:30–14:00 Course Conclusion, Certification & Next Steps
Final reflection, distribution of resources, and commitment to action plan implementation.
RESULTS
Developing and implementing a Privacy-by-Design approach across all school operations.
Conducting internal audits to identify and mitigate vulnerabilities at every stage of the Data Lifecycle.
Securing cross-border mobility projects (Erasmus+) against both physical and digital security threats.
Immediately recognizing and responding to AI-driven threats like deepfakes and advanced phishing attempts.
Training staff and students on responsible digital citizenship and visual privacy standards.
Critically evaluating and safely adopting new EdTech tools while ensuring student data remains protected and compliant with GDPR.
Implementing mandatory, effective network and device safeguards (MFA, access control).
Course Format
One-week length: two weeks or other formats are available on request.
4-5 hours per day: from Monday to Friday, with excursions planned during the training.
Fully fundable: Meeting the Erasmus+ KA1 budget criteria.
Flexible: change courses, locations, or dates without fees.
Audience and requirements
Courses are structured around the collective sharing of participants’ experiences, therefore all courses are in English. For participants with a very low English level, we advised to come with a translator in the team.
We provide tailored courses for school roles like teachers, principals, and staff, as well as for different levels of IT skills. Our programs are designed to meet the unique needs of professionals such as adult educators, language teachers, youth workers, and social workers, ensuring they have a meaningful impact in education and social work.
€80/Day
Our services include:
✔ Infopack about the location
✔ Pre-arrival information.
✔ Tuition & training materials.
✔ Coffee break.
✔ Training Certificate.
✔Europass Certificate.
✔ Admin & organisational costs.
Additional Services:
✔ Accommodation options, including hotels and self-catering apartments
✔ Half-day and full-day trips
✔ Cultural experiences and local activities
✔ Airport transfer services
✔ Local transportation arrangements
Our Pricing:
100% funded by the Erasmus Plus Program
Fill out our contact form, and we’ll respond to you promptly.